VIAVI Threat Exposure Management
Observer Sentry has redefined cloud threat exposure management,
giving you the visibility you need to quickly identify, prioritize, and
remediate threats prior to being compromised.
The VIAVI Threat Exposure Management solution analyzes and visualizes your AWS environment to help you pinpoint where and why cloud assets are most vulnerable to attack.
Exposure is inevitable, but it’s not always bad. What may appear to be an undesired exposure may simply be a necessary part of a service architecture and service delivery. The VIAVI Observer Sentry approach to Threat Exposure Management (TEM) seamlessly combines the power of agentless technology, operationalized diagrams, and advanced automation to analyze and quantify your threat exposure and keep you two steps ahead of attackers. TEM insights also allow you to identify and mitigate the unintended exposure paths or overly permissive settings that can put assets at risk, or validate that things are configured properly and secured as designed.
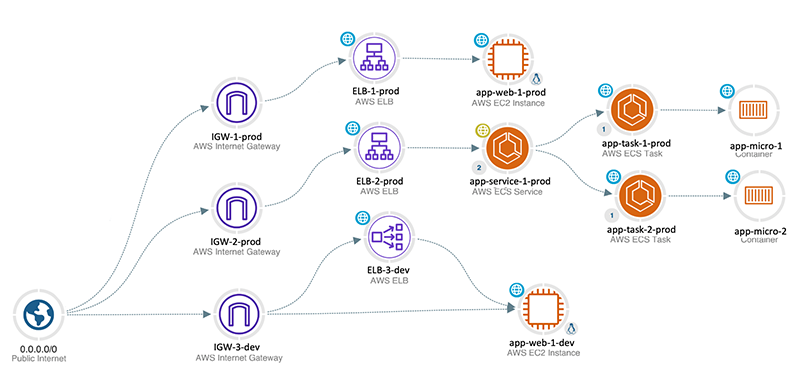
Attackers think in graphs, not lists. Think like your adversary. The Threat Exposure Management approach taken by VIAVI changes how you view your environment, taking you from lists, configuration details, and logs to a visualization of your AWS environment from the attacker’s perspective. Observer Sentry identifies connections and interdependencies that linear protection strategies can miss, allowing you to visualize the relationships between assets and prioritize the most critical risks.
The Need for Exposure Management is on the Rise
“Through 2026, more than 60% of threat detection, investigation, and response (TDIR) capabilities will leverage exposure management data to validate and prioritize threats, up from less than 5% today” – Gartner Predicts 2023: Enterprises Must Expand from Threat to Exposure Management
The list of available threat detection tools and approaches grows longer each year, making it hard to decipher which ones bring the most value and how they interrelate. The volume of security incidents and notifications being generated is overwhelming. Applying Continuous Threat Exposure Management is critically important and helps address multiple challenges and needs.
- Reducing Attack Surfaces. Attack surfaces are the sum of all attack vectors that cybercriminals use to gain unauthorized access. Much like a physical attacker searching for weaknesses in infrastructure or surveillance practices, cybercriminals seek to identify the weak points in attack surfaces to establish new attack paths. TEM continually shrinks the attack surface by systematically identifying and analyzing potential attack paths giving you the visibility you need to prioritize and remediate the risks.
- Vulnerability Management enhances endpoint protection by scanning individual devices or machines for weaknesses that might allow them to be exploited or breached. Unpatched operating systems and applications commonly contribute to identified vulnerabilities but the challenges around remediating the vulnerabilities are significant. In fact, in The State of Vulnerability Management in DevSecOps report by the Ponemon Institute, 66% of respondents indicate their backlog consists of more than 100,000 vulnerabilities. Many factors contribute to this challenge but lack of exposure context and the need for enhanced prioritization strategies both play a significant role.
- Overly permissive settings grant unnecessary or unsafe access to systems, networks, or applications. These permissive access policies stand in stark contrast to emerging zero-trust that only grants access to services or ports when necessary.
Threat Exposure Management allows you to mitigate the dangerous combination of exposure, vulnerabilities, and permissive settings that create a clear path of least resistance for attackers. The holistic TEM approach uses continuous, automated analysis to proactively identify these potential exposures and threats while providing more visibility and protection than platforms focusing on vulnerabilities alone.
“Threat exposure management…expands beyond patches and automated blocking to better prepare against unpredictable threats and strategically reduce the enterprise’s attack surface” – Gartner Predicts 2023: Enterprises Must Expand from Threat to Exposure Management
Threat Exposure Management Pain Points
TEM addresses many of the common security pain points customers encounter as they strive to keep up with ever-changing cloud environments and service architectures:
- Visibility Gaps: Ongoing human, system, and design changes make a passive approach to visibility unsustainable. Locking down systems reactively does not fully account for the interactions and permissive settings that may be creating new attack vectors.
- Siloed Views: The elimination of siloed views is one key to optimizing visibility. With customers maintaining multiple AWS accounts, monitoring each individually is neither efficient nor adequate. Observer Sentry’s approach to Threat Exposure Management allows you to view all accounts and the interrelationships between them simultaneously.
- Automated Changes: Automation has heightened the pace of change in the end-to-end AWS environment faster than human abilities can comprehend. TEM platforms incorporate their own advanced automation and agentless technology to counter this speed with actionable context.
- Data Volume: Critical insights and vulnerabilities can be obscured by the sheer volume of data, potentially leading to extensive delays in detecting and mitigating issues. The pace of data flow also makes it challenging to isolate anomalies without the benefit of intelligent algorithms.
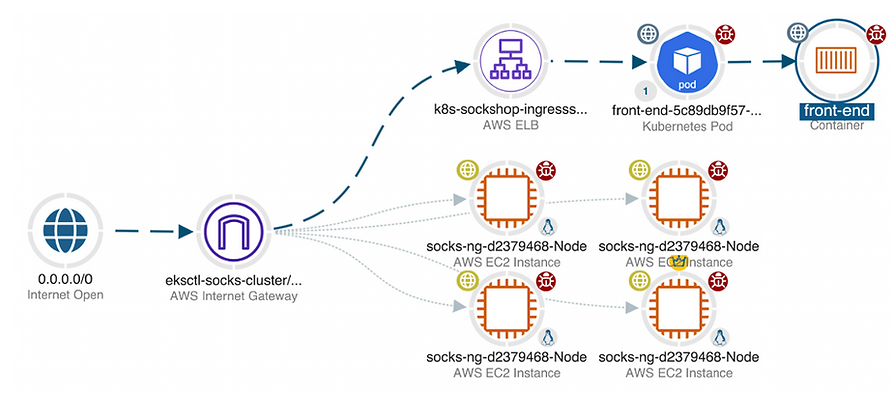
The VIAVI Approach – Delivering Clear Value
Threat Exposure Management allows you to harden applications and the overall AWS environment by continually reducing the attack surface. Observer Sentry addresses TEM challenges by enhancing exposure visibility; presenting intuitive and actionable visualizations and reports highlighting risky combinations of exposure paths and vulnerabilities allowing users to identify where to mitigate the risk prior to being compromised.
- Operationalized Diagrams are intuitive cross-environment graphical tools that quickly identify misconfigurations and overly permissive settings in an easily digestible visual format. Graph-based technology allows your entire team (including DevOps and Application Owners) to maintain visibility while developing an in-depth understanding of the full cloud stack.
- Agentless Technology scans the entire cloud environment automatically to map all assets and their relationships. The AWS environment and its EKS and ECS clusters are continually scanned to ensure cross-environment maps represent the latest threat exposure conditions.
- Scorecards provide a snapshot of system health and exposure levels for each application, logical asset grouping, workload, or environment. Application owners can easily filter scorecards to review their areas of responsibility. Exposure findings and coverage are expressed in percentages to provide a basis of comparison while vulnerabilities and business criticality are color-coded based on severity.
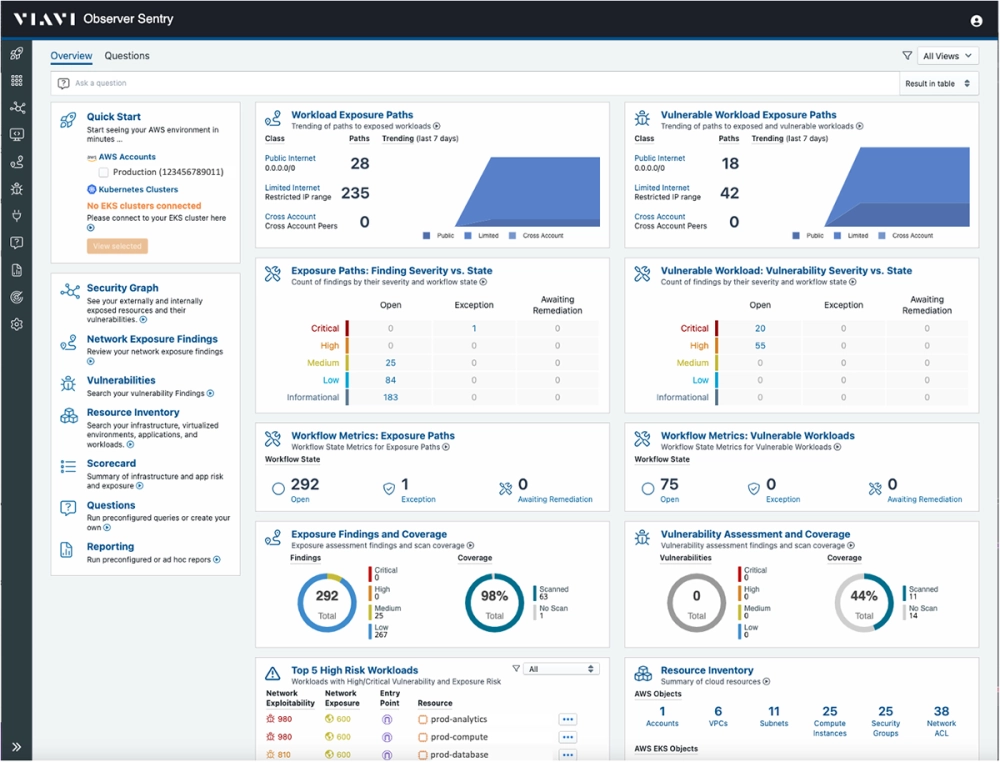
Threat Exposure Management Use Cases
Across all industries, AWS customers find significant benefits and enhancements by leveraging multifaceted TEM insights and capabilities.
Threat Exposure Management – Answering the Critical Questions
Asking the questions that impact cybersecurity most will lead you to solutions that provide the greatest protection. Observer Sentry helps you answer these important questions consistently and confidently:
- How does an attacker see my cloud environment?
The attack path analysis and advanced graph theory algorithms of Observer Sentry identify relationships between otherwise siloed security findings to continuously visualize your cloud environment from the attacker’s perspective and prioritize remediation of critical security gaps. - Where are my cloud assets at risk?
Observer Sentry creates a detailed inventory of your cloud assets and performs an analysis to determine their attack surface, effective exposure, and risk. This analysis can also be applied collectively to logical groupings of assets. - Which paths can attackers exploit?
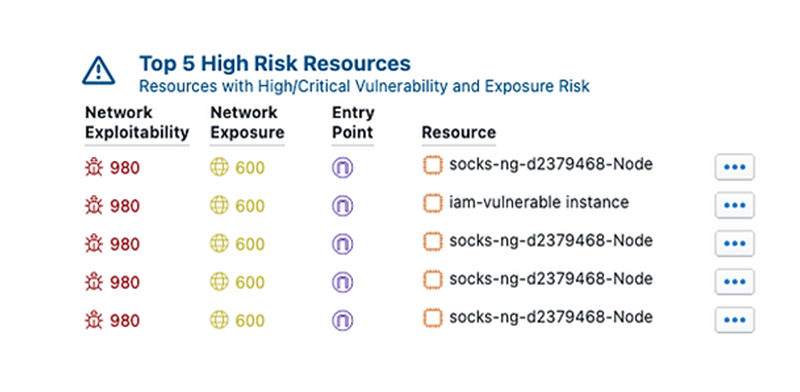
By quickly analyzing exposure paths from various points of entry and identifying unknown or undesired access to assets, the most exploitable paths are identified so that corrective actions can be initiated proactively. Scorecards and attack surface maps provide useful visual context and can be further enhanced with 3rd party integrations. - What do I fix first?
Observer Sentry continuously prioritizes critical risks based on the analysis of misconfigurations, network exposure, and vulnerabilities identified by 3rd party scanners and creates a prioritized list of risks for your cloud environment.
The VIAVI Observer Platform
Observer Sentry is part of the VIAVI Network Performance Management and Threat Solutions portfolio and the Observer Platform.
The VIAVI Observer Platform provides visibility into critical KPIs through pre-defined workflows and high-level dashboards. The versatile Observer Platform is optimized to support business goals while overcoming resource, technology, security, and asset management challenges throughout the IT enterprise lifecycle.
