Utel Fraud Management System
Empowering telecom operators to detect, prevent, and block fraudulent traffic
Fraud Management System (FMS)
Utel offers cutting-edge anomaly detection solutions based on AI/ML designed to safeguard your customers and ensure regulatory compliance. Our advanced tools empower telecom operators to prevent, detect, and block fraudulent traffic.
Anomaly Detection Engine Protects Your Customers
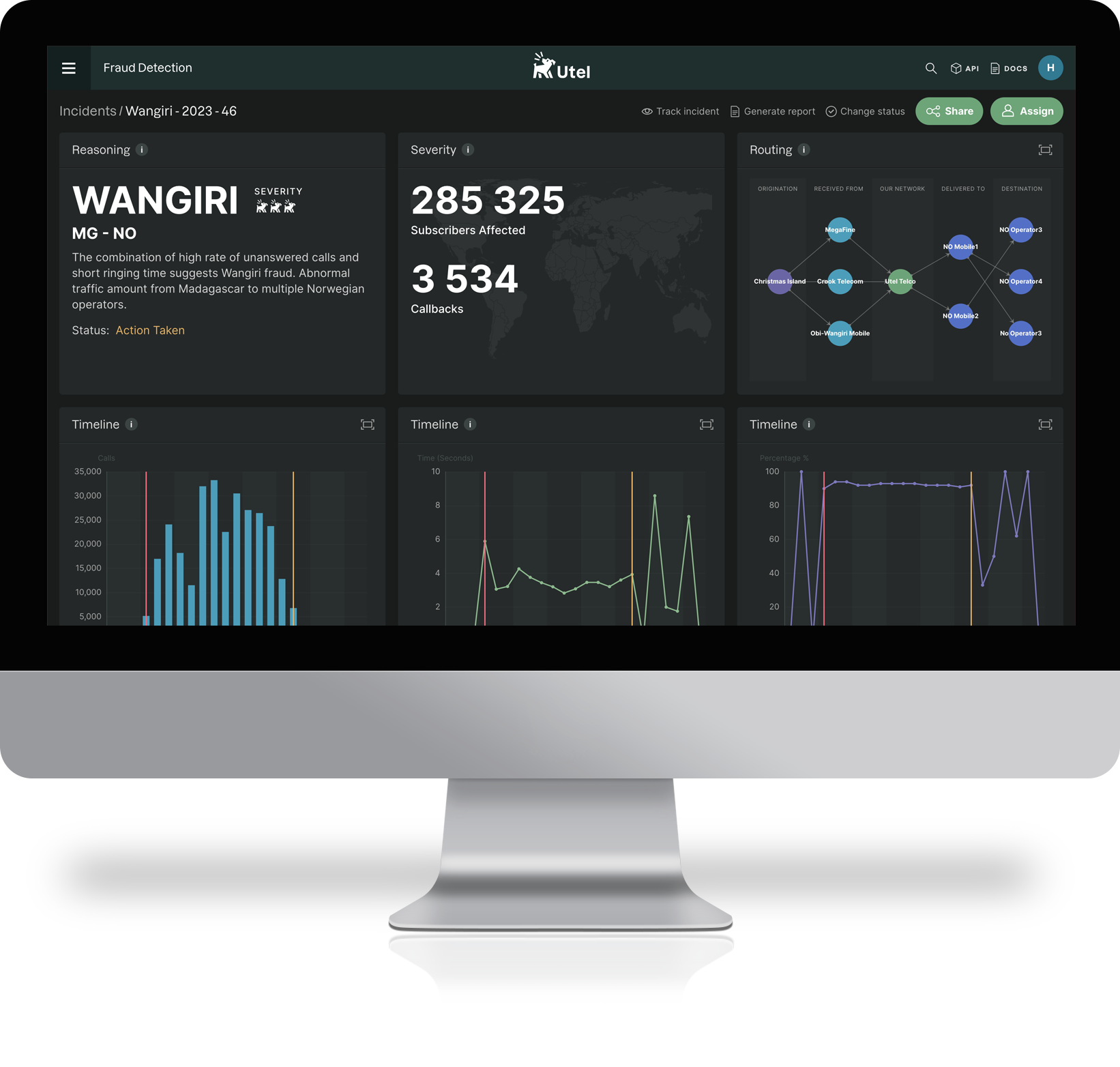
The Utel Fraud Detection engine utilizes our market-leading Network Monitoring technology to detect and resolve telecoms messaging and voice fraud.
The solution deploys virtual network probes that harvest calling data directly, generating Call Detail Records (CDRs) that provide a complete overview of the messaging and voice traffic across the network to quickly identify suspicious activities and patterns.
The data collected is analysed in real-time, and our exclusive algorithms identify fraudulent traffic profiles. Dynamic alarms and alerts are generated, enabling rapid escalation to the anti-fraud team for urgent investigation. Utel Fraud Detection delivers immediate results and ROI – increasing customer satisfaction, reducing losses due to fraud, and reducing churn.
Key Features
Machine Learning Enhanced
As fraudsters evolve their tactics and new risks emerge, our unsupervised machine learning algorithms provide robust protection against emerging threats.
Trend Visualization
Advanced filtering and analysis not only puts information at your fingertips but delivers clear visualization of fraudulent behaviours to provide immediate and clear insights into threats.
Automated Notifications
When threats are detected, the anti-fraud teams receive automatically alerts, enabling fast termination of number ranges across the network and reducing customer fraud.
Location Identification
Calls from a single-number series, based on the Calling Line Identity (CLI), are identified by the solution, so you can identify the operator sending specific traffic into your network.
Enhanced Analysis
By analysing summaries from both the called and calling phone numbers and by looking at an aggregate of all the traffic in the network, threats are automatically discovered by the solution.
Filter, Sort, and Categorise
Quickly identify fraudulent calls by specific characteristics such as calls that terminate in specific number series or known fraudulent number series.
